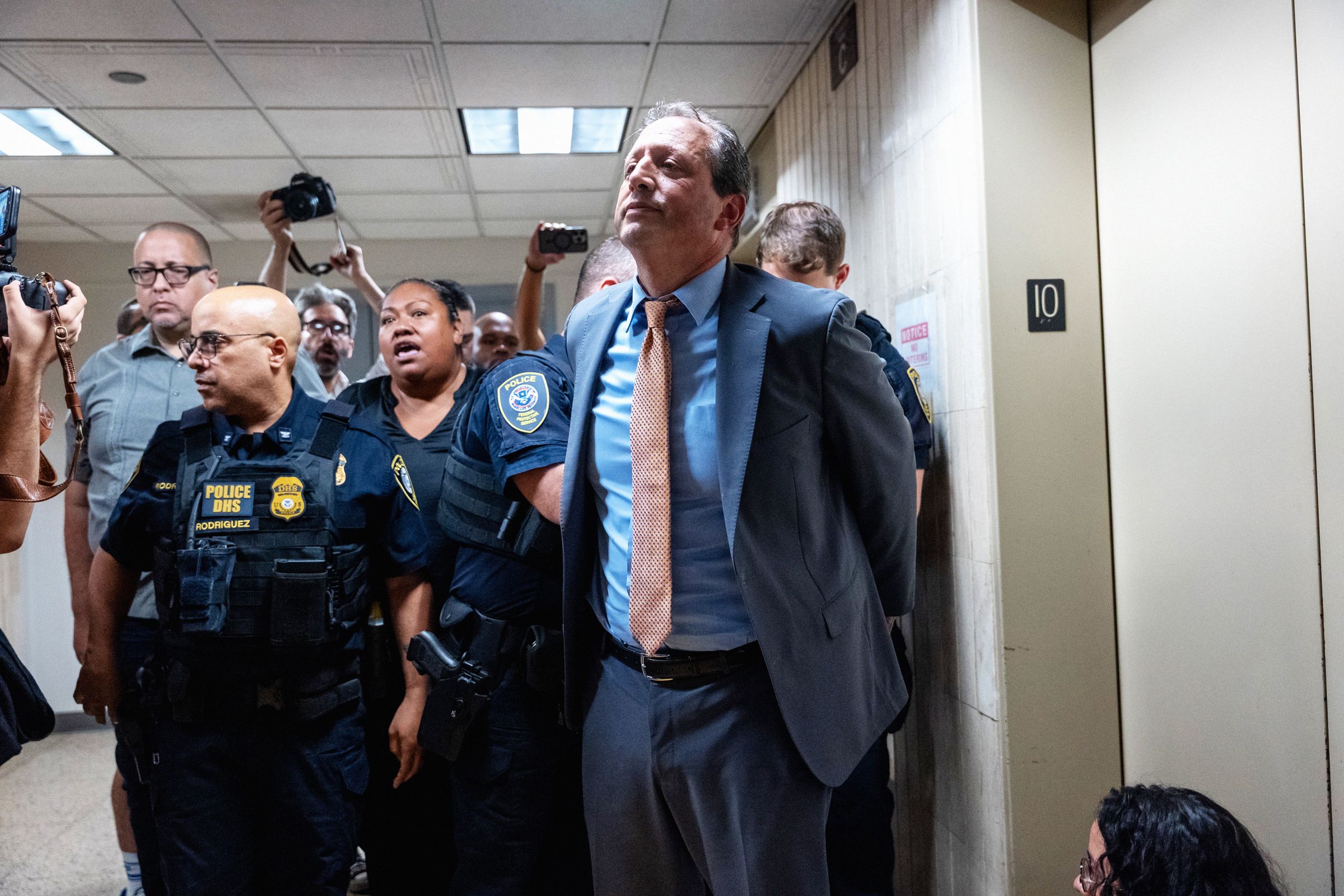A Cyberattack on Jaguar Land Rover Is Causing a Supply Chain Disaster Recently, Jaguar Land Rover announced that they have...
Security
Google's Latest AI Ransomware Defense Only Goes So Far Google's Latest AI Ransomware Defense Only Goes So Far Google's latest...
Jeffrey Epstein’s Yahoo Inbox Revealed The contents of Jeffrey Epstein's Yahoo inbox have been leaked, shedding light on the communications...
Tile Tracking Tags Can Be Exploited by Tech-Savvy Stalkers, Researchers Say Researchers have found that popular Bluetooth tracking tags, such...
Cybercriminals Have a Weird New Way to Target You With Scam Texts In today's digital age, cybercriminals are constantly finding...
This Microsoft Entra ID Vulnerability Could Have Been Catastrophic Last month, cybersecurity experts uncovered a major vulnerability in Microsoft's Entra...
How to Use 1Password's Travel Mode at the Border (2025) How to Use 1Password's Travel Mode at the Border (2025)...
A DHS Data Hub Exposed Sensitive Intel to Thousands of Unauthorized Users A DHS Data Hub Exposed Sensitive Intel to...